At the time of writing this article, it has been reported that a new variant of this malware Rustock. They were the ones to use Trojans written in Java Trojan-Downloader. If it had been provided, this file could have significantly simplified the work carried out by other antivirus laboratories to analyze the rootkit and develop procedures to detect and treat Rustock. A makes use of IRP patching for two main reasons: The DLL code spambot differs slightly from variant to variant. You should download the definitions from the Symantec Security Response Web site and manually install them. How to verify that a Symantec Corporate antivirus product is set to scan all files. 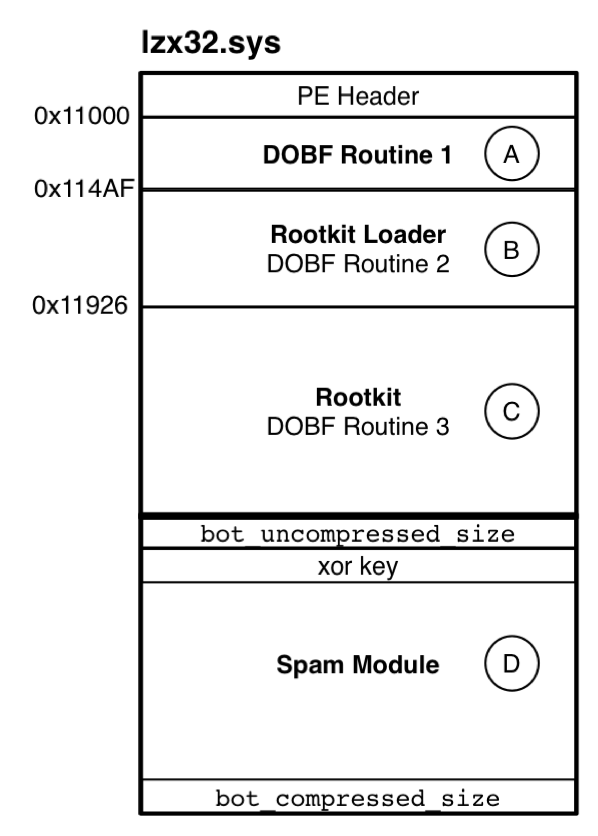
| Uploader: | Dogami |
| Date Added: | 15 July 2015 |
| File Size: | 40.34 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 71128 |
| Price: | Free* [*Free Regsitration Required] |
A Case Study of the Rustock Rootkit and Spam Bot
Nikolaos Tsapakis explores Network Time Protocol NTP as an alternative communication channel, providing practical examples, code, and the basic theory behind the idea.
Rootikt shows in the left-hand column all the typical anomalies detected by rootkit detectors and in the right-hand column the countermeasures adopted by Rustock. C that were circulating widely as far back as the end of ? Retrieved August 25, It appears that whoever created the rootkit was rootit confident of its effectiveness that they did not attach much importance to thwarting antivirus protection.
Rustock botnet
Leaping ahead of the story, I can say that we never found any samples of Rustock. Summary Technical Description Removal. This change is targeted specifically towards Kernel SC, a tool used to detect the presence of hidden services. McColo regained internet connectivity for several hours and in those hours up to 15 Mbit a second of traffic was observed, likely indicating a transfer of command and control to Russia.
Rustock and All That | Securelist
Yes, we are once again facing one of the best-known cybercriminal groups on the Internet and the names above are associated with its websites and malicious programs. Your email address will not be published. Invisible module in Windows kernel. Creates the following file: When prompted for a root or UAC password, ensure that the program asking for administration-level access is a legitimate application.
Now we know in detail how and from which servers it was downloaded and installed on computers. Also, a virus scan may detect a threat in the System Restore folder even though you have removed the threat. The never-ending game of hide-and-seek between the anti-virus industry and rootkits has begun a new chapter. The following names will be familiar to every antivirus expert:.
Recommendations Symantec Security Response encourages all users and administrators to adhere to the following basic security "best practices": How to make a backup of the Windows registry.
It uses a mixture of old techniques and new ideas that, when combined, make a piece of malware that is stealthy enough to remain undetected by many commonly used rootkit detectors such as RootkitRevealer, BlackLight, IceSword, DarkSpy and GMER. It was created after a promotion of sorts in rootkit researcher circles — possibly, in response to the hysteria that accompanied the search for it. We believe that Rustock.
In an average five-year-old car, there are about 30 different computers on board. Disable anonymous access to shared folders. The botnet rustoock a hit after the takedown of McColoan ISP which was responsible for hosting most of the botnet's command and control servers. Retrieved from " https: C is currently blocked.

Views Read Edit View history. Leave a Reply Cancel Reply Your email address will not be published. The following instructions pertain to all current and recent Symantec antivirus products, including the Symantec AntiVirus and Tootkit AntiVirus product lines. To delete the value from the registry Important: Warning messages may be displayed when the computer is restarted, since the threat may not be fully removed at this point.
The Rustock installer comes as an executable file with a size of around 65—70 KB and is root,it by a polymorphic packer which mixes NOP-equivalent and floating-point opcodes together with real instructions. If write access is not required, enable read-only mode if the option is available.


No comments:
Post a Comment